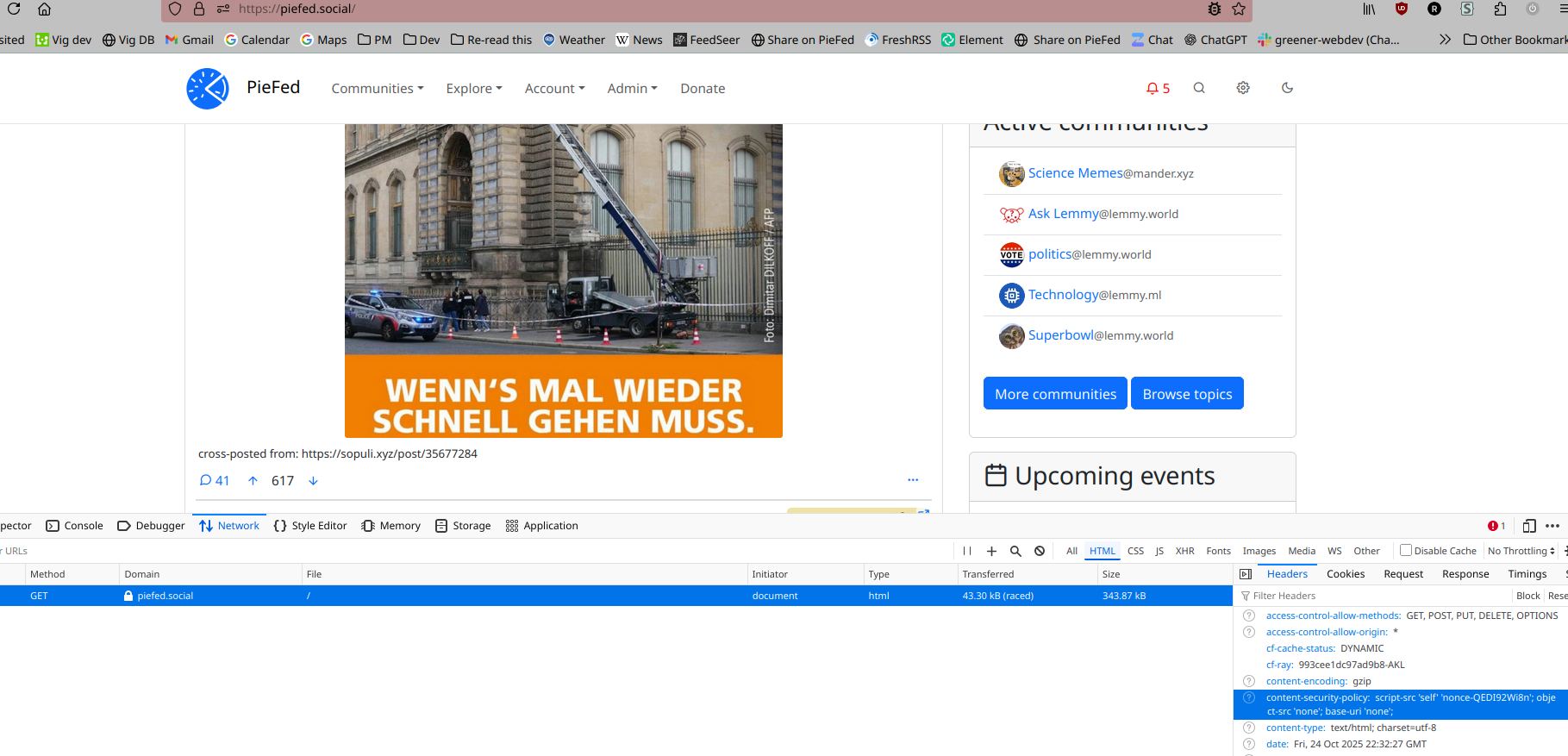
So, I just visited your instance and there is definitely an issue...but I am not sure I will really be of much help. When I click an image, it looks like the lightbox javascript is being blocked by the CSP. Here is what I see in the browser console:
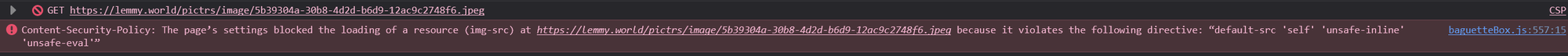
The CSP that ships with piefed should allow the lightbox to run without issue. Perhaps there is a reverse proxy or CDN applying a stricter CSP? Maybe a browser plugin of some kind?
This kind of web admin stuff isn't really my area of expertise though.